A website is not just a standalone application. It’s comprised of folders, directories, and pages that carry instructions and information for a particular task or request. When you interact with a website, you are led through a series of directories. But not all directories are visible to you; some are hidden from the public. How do hackers get to know about hidden directories and exploit them?
What Is Directory Bursting?
Directory bursting (also known as directory brute forcing) is a web application technology used to find and identify possible hidden directories in websites. This is done with the aim of finding forgotten or unsecured web directories to see if they are vulnerable to exploitation.
How Does Directory Bursting Work?
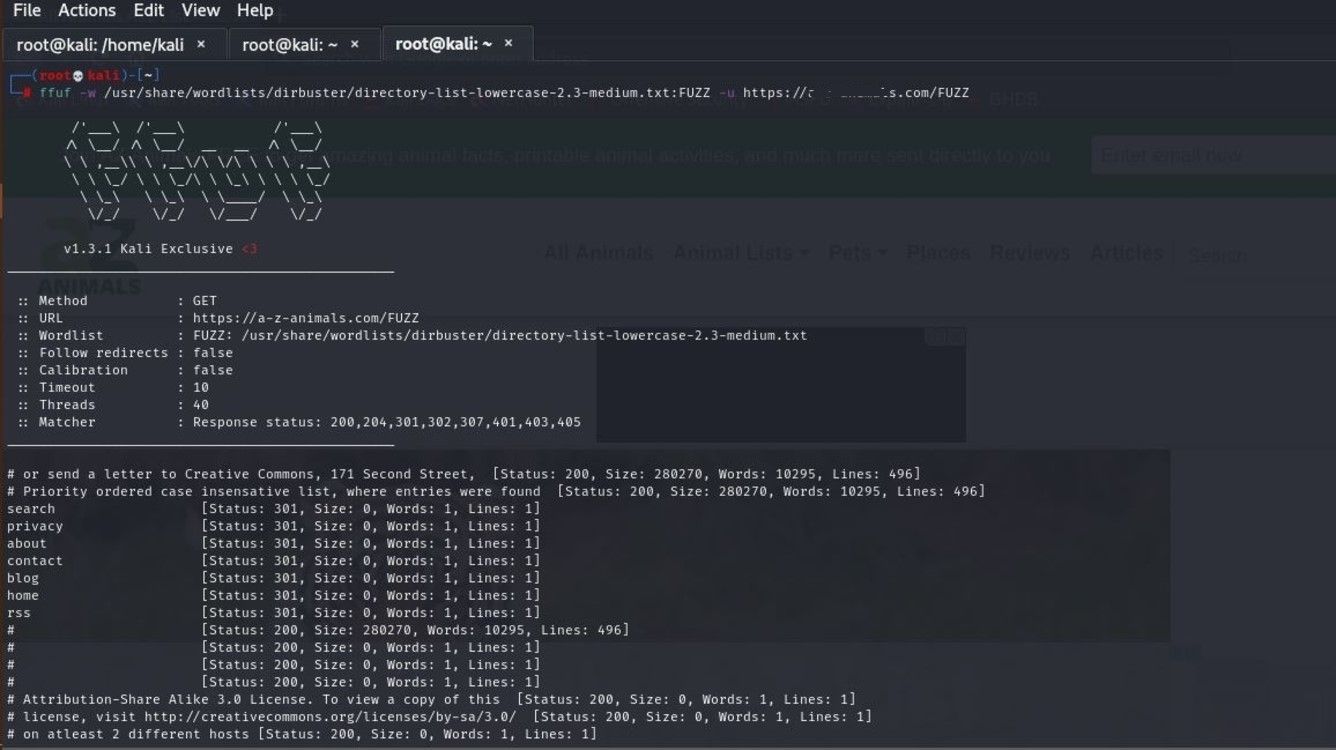
Directory bursting is carried out using a combination of automated tools and a collection of scripts called wordlists. Some of these tools include Gobuster, Dirb, FFUF, Dirbuster, etc. How does directory bursting work?
What Is a Directory?
A directory is a folder or collection of files containing information. It is used for organizational purposes and utilizes a hierarchical system. Web applications are made up of many directories and subdirectories and these in turn are used to store information like static HTML files, servlets, CSS and JavaScript files, external libraries, images, etc.
For example, the MakeUseOf page of an author could read “www[dot]makeuseof.com/author/author-name/page/2/” if you were on the second page of the author’s profile. The name of the site or the root directory is “www[dot]makeuseof.com”. It has a subdirectory that stores authors’ profiles and works named “/author/”. This directory has another subdirectory containing the works of that particular author. Then, the next directory contains the page number you are on.
Directory Bursting Tools and Wordlists
Manually typing in hundreds of directory names into a website to scan for possible hidden directories would be a time-consuming and futile task. Instead, hackers use tools alongside wordlists to automate directory bursting attacks. These automated tools are usually multithreaded and work by making an HTTP or HTTPS request of each file name in the wordlist. If the directory name exists, the response code and name are recorded and shown.
A directory bursting or brute-forcing tool is only as good as the wordlist. A wordlist, as the name implies, is usually a .txt file that contains thousands of possible names of directories and files to be scanned by the directory brute-forcing tool . There’s a huge number of wordlists available on the internet, and many directory bursting tools come with in-built ones too.
To brute force a website’s directories, you need the URL of the website and a wordlist. Some directory bursting tools provide options like speed, file extensions, or allow you to specify what level of directories to scan or hide specific words.
How to Protect Your Website From Directory Bursting
Directory bursting or brute-forcing itself is not harmful, as it just enumerates the hidden directories you might have on your website. It is the information that a hacker might find in those directories that creates vulnerabilities in your website. If you store sensitive information like source code or databases in directories without enforcing proper permissions, hackers would be able to exploit that.
And anyone can be vulnerable: even Microsoft’s source code was leaked!
The most common vulnerability that might arise from directory bursting is the directory or path traversal vulnerability. This vulnerability allows a hacker to access files and directories they normally shouldn’t have permission to do so. With directory traversal, hackers are able to read and sometimes rewrite arbitrary files on the web application. They do this by escalating privileges from user privileges to root privileges.
Here are some tips to protect your websites from directory bursting vulnerabilities:
- Enforce file and directory permissions.
- Always validate users and user input.
- Keep your servers and the infrastructure behind them up to date.
Directory brute-forcing not only identifies hidden directories in your website, but also provides information on the structure of your website—information that could prove useful to a skilled hacker.
Directory Bursting and Ethical Hacking
Ethical hackers use directory bursting tools to mitigate vulnerabilities before a cybercriminal finds them. Directory bursting is important in the enumeration phase of a web penetration test, and it can improve the security of a website by finding information on a web service that shouldn’t be accessible to the public and removing them.